Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

Security breaches are what nightmares are made of. You probably have your own ‘nightmares’ that come to mind. Tesla was hacked because their Kubernetes administrative console was not password protected. In another incident, Capital One left their AWS firewall definitions too lax and 30GB of credit application data (affecting 106 million customers) was exposed.
Aside from implementing Kubernetes itself, the single most important consideration is security. Roughly 60% of Kubernetes security breaches are due to misconfiguration.
State of Kubernetes Security 2021
Security is as complex as it is important. The expertise that’s needed to manage your security needs effectively is considerable, and poses to overwhelm your teams and the amount of effort you can feed it.
It’s a big subject but, reduced to its simplest form, managed Kubernetes can be broken into five security layers:
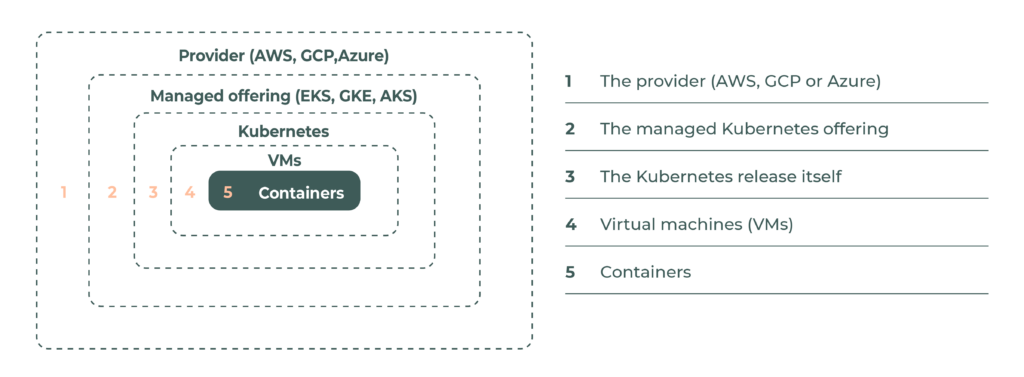
Each layer has its own security definitions and configurations and needs to be managed properly to make sure it works with the other layers. There are best practices to consider for each layer individually as well.
When you start dealing with multiple cloud vendors, more complications start to arise. The security definitions on Azure have some similarities with definitions on Google Cloud Platform (GCP) or Amazon Web Services (AWS), but they are not the same. Knowing how to build a cluster on EKS does not guarantee you can easily tackle standing up a secure AKS cluster. From a security perspective, supporting multiple providers will magnify operational pain because of the diversity of expertise needed.
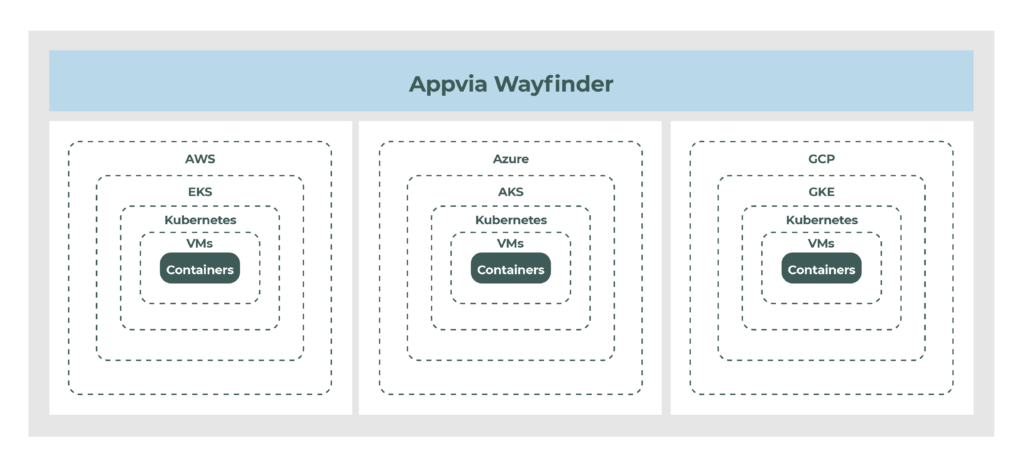
Appvia Wayfinder simplifies security configuration by implementing a predefined set of options. It sits on top of the provider’s interface, understands the different security configurations and fulfills best practices across all of the layers mentioned above.