Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

As organisations increasingly embrace the cloud, establishing a robust and standardised environment becomes crucial. Azure Landing Zones provide a structured approach to creating a foundation for deploying workloads in Microsoft Azure.
To recap what we covered in our previous blog <link to blog>, a landing zone is a well-architected environment that is highly scalable and secure. A landing zone allows you to accelerate moving workloads to the cloud whilst maintaining control and ensuring appropriate guardrails are in place. It is your cloud foundation, designed according to a set of best practices and guidelines, with a focus on key elements such as account and resource organisation, access management, network architecture, security and compliance, and logging/monitoring/auditing.
Azure Landing Zones adhere to these essential principles, including scalability, modularity, and security. These principles span eight key areas:
Each key design area provides you with a set of guidelines and questions to consider when designing your own Landing Zone.
Whilst Azure makes it very easy to get started in the Cloud, things can quickly get out of hand. Costs can quickly spiral, resources can be deployed in an insecure way and adoption can be difficult to scale and support.
Adopting Azure Landing Zones brings the following benefits to your organisation:
The following diagram from Microsoft gives an opinionated target architecture for your Azure landing zone architecture and can be used as a starting point to tailor to your organisation’s needs:
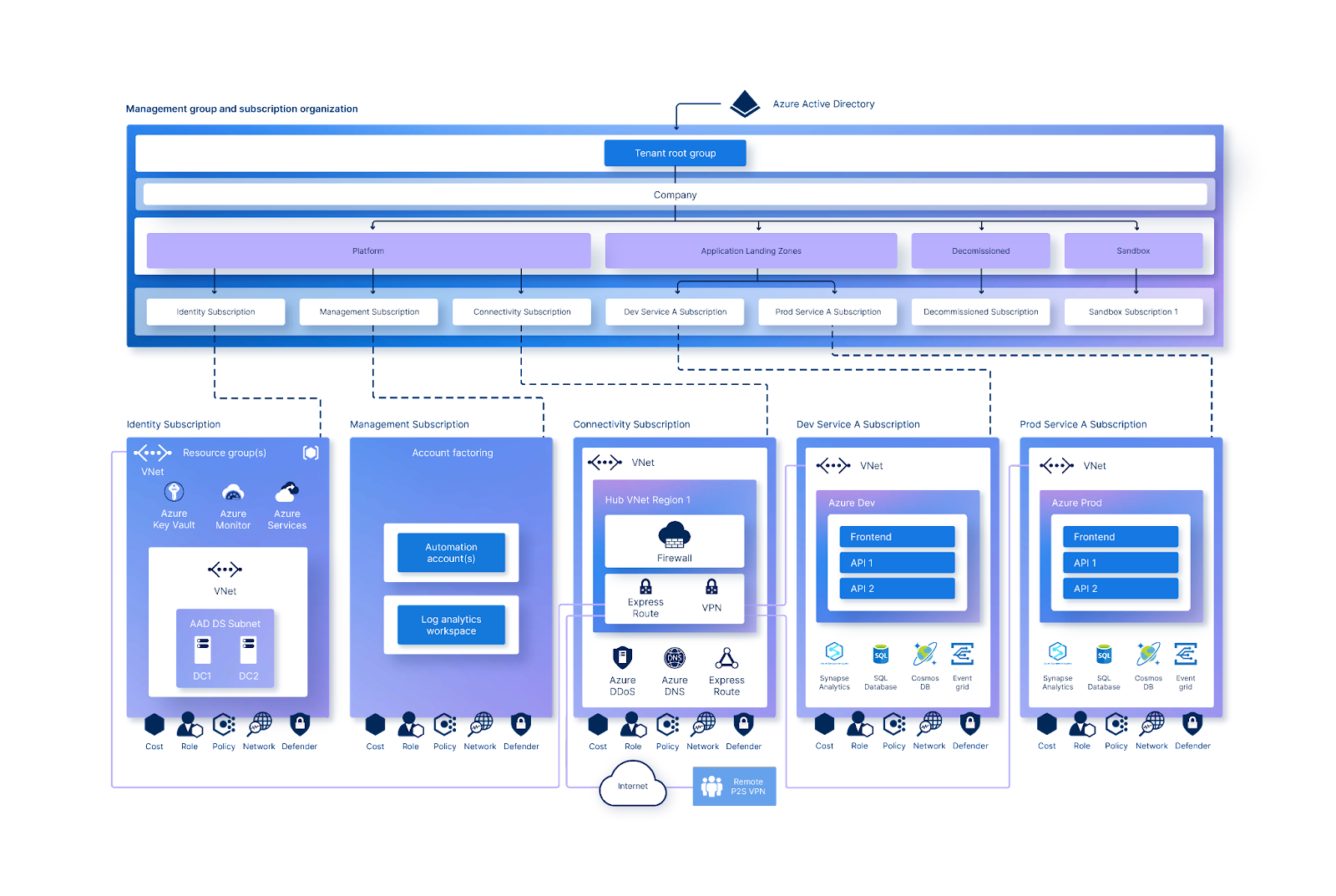
There’s a lot going on in this diagram, so let’s break it down into the individual areas:
Microsoft has developed a very comprehensive library of documentation to explain each of the design areas in detail. Rather than repeat what’s already been written, I’ll give a summary of each of the areas.
Azure billing and Microsoft Entra tenants: This design area focuses on setting up proper enrollment and billing for your organisation’s Azure environment. It’s important to create a Microsoft Entra tenant (previously Azure Active Directory), to manage access to your organisation’s resources. Whilst it’s possible to create multiple tenants, the advice is to use a single tenant across your organisation to avoid unnecessary friction and confusion for your users. This relates to item A in the conceptual diagram.
Identity and access management: This design area is concerned with managing identities and access to resources in the cloud. It’s important to establish a secure identity foundation to ensure that only authorised users have access to your organisation’s resources. Identity and access management lets the right individuals access the right resources at the right time for the right reasons. Azure offers a comprehensive set of services, tools, and reference architectures to help organisations make highly secure, operationally efficient environments. This relates to item B in the conceptual diagram above.
Resource organisation: This design area is focused on organising your subscriptions and management groups to ensure that your cloud environment is scalable and manageable. It’s important to establish a clear hierarchy of management groups and subscriptions to ensure that your governance and compliance policies are enforced. This allows you to put the appropriate Policy-driven guardrails in place at the right levels to ensure that your subscriptions are manageable. This relates to item C in the conceptual diagram above.
Microsoft recommends keeping the hierarchy reasonably flat, ideally with no more than three to four levels. This separates subscriptions into:
Network topology and connectivity: This area is concerned with designing the network topology and connectivity for your cloud environment. The goal of network design is to align your cloud network design with overall cloud adoption plans, whether these include hybrid or multicloud dependencies or other connectivity. This relates to item E in the conceptual diagram.
Security: This design area creates a foundation for security across your Azure, hybrid, and multicloud environments. Security is a core consideration for all customers, in every environment. When designing and implementing an Azure landing zone, security should be a consideration throughout the process. This relates to item F in the conceptual diagram.
Management: This design area is focused on establishing a management baseline to provide visibility, operations compliance, and protection and recovery capabilities across Azure, hybrid, or multicloud environments. It’s important to establish a monitoring and management framework to ensure that your cloud environment is stable and secure. This relates to items D, G and H in the conceptual diagram.
Governance: This design area is focused on establishing a secure and compliant cloud environment. It’s important to establish a security and governance framework to ensure that your organisation’s resources are secure and compliant with industry standards and regulations. This relates to items C and D in the conceptual diagram.
Platform automation and DevOps: This design area is concerned with automating the deployment and management of your cloud environment. It’s important to establish a DevOps culture to ensure that your organisation can quickly and efficiently deploy new resources and applications. This relates to item I in the conceptual diagram.
Here are some common challenges that organisations face when implementing Azure Landing Zones:
We would always recommend using the Microsoft Infrastructure As Code (IaC) accelerators, e.g. Terraform, to give your organisation the best chance of success. Additionally, Microsoft provides lots of guidance on how to tailor the Azure landing zone architecture to meet specific requirements.
When it comes to setting up Azure Landing Zones, there are three main approaches:
Do It Yourself: Tailor the architecture to your specific needs. Design your landing zones from scratch, considering your organisation’s unique requirements.
Pre-Built Solutions: Microsoft offers various Azure Landing Zone Accelerators. It’s like having an expert architect guide you. The accelerators provide opinionated target architectures, templates, and scripts. You can start with these and then customise as needed.
Bring in an expert: At Appvia we’ve helped many organisations implement Cloud Landing Zones. Our solutions are built on Microsoft’s Cloud Adoption Framework, the Azure Landing Zone Accelerator and our experience helping organisations like yours. We work with your organisation to understand your requirements and implement the right solution to accelerate your journey to the Cloud.
Azure Landing Zones offer a structured approach for deploying workloads in Microsoft Azure, ensuring scalability and security.
Benefits of adopting Azure Landing Zones include standardisation, confidence in cloud adoption, operational efficiency, and enhanced security and compliance.
They adhere to essential principles across eight key design areas, including billing, identity management, resource organisation, network design, security, management, governance, and automation.